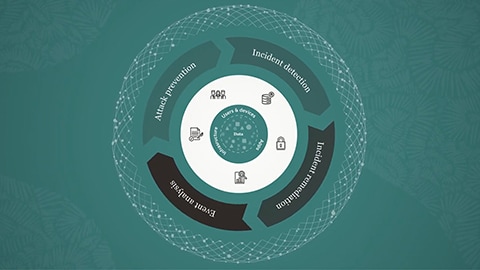
Data breach prevention in the cloud is crucial to safeguarding sensitive information online. To ensure your cloud data remains secure, it’s important to implement robust security measures and follow best practices for cloud computing.
With the rise of remote online work, cloud computing has become increasingly popular, offering easy access to data and collaboration tools from anywhere. However, this has also increased the risk of data breaches. To prevent data breaches, several measures can be taken, such as using strong passwords, encrypting data, and implementing multi-factor authentication.
This article will explore in-depth ways in which you can safeguard your data in the cloud, outlining specific strategies and practices to help you prevent unauthorized access, theft, or loss of data. By following these guidelines, you can keep your sensitive information safe and secure in the cloud.

Credit: www.kaspersky.com
Understanding Cloud-Based Data Breach Prevention
Data breaches are a concern for businesses globally, especially with the increasing amount of data being stored in the cloud. In this blog post, we’ll talk about cloud-based data breach prevention and the advantages of using cloud-based solutions over traditional methods.
Additionally, we’ll explore how these solutions help prevent data breaches in the cloud.
Definition Of Cloud-Based Data Breach Prevention
Cloud-based data breach prevention refers to the security measures businesses take to protect their confidential information from unauthorized access, theft, or damage. Cloud-based data breach prevention differs from traditional data breach prevention methods since the data is stored in a cloud rather than an on-premise location.
Advantages Of Using Cloud-Based Solutions Over Traditional Methods
- Scalability: Cloud-based solutions offer scalability, which means businesses can scale up or down according to their needs effortlessly. As the demand for resources increases, cloud-based solutions can provide additional resources on demand.
- Affordability: Cloud-based solutions offer an affordable alternative to traditional data breach prevention methods. Businesses do not have to spend as much money on hardware, software, or personnel.
- Accessibility: Cloud-based solutions allow businesses to access data from anywhere in the world as long as they have an internet connection. There are no geographical barriers to data access, which makes collaboration easier.
How Cloud-Based Solutions Work To Prevent Data Breaches
Cloud-based solutions work to prevent data breaches by implementing a multi-layer security system. The following are the layers of protection:
- Authentication: Cloud-based solutions require users to authenticate themselves before accessing their data. Authentication can include various factors such as passwords, pins, biometric authentication, or multi-factor authentication.
- Encryption: Encryption ensures that data is unreadable to anyone who isn’t authorized to access it. Cloud-based solutions use both at-rest and in-transit encryption methods.
- Monitoring: Cloud-based solutions monitor access to data and identify any anomalous behavior. Any suspicious activity triggers alerts, which are then investigated to determine if they are a threat.
- Backups: Cloud-based solutions also provide backups of data, which can be restored in case of data loss. Backups ensure that data is not lost or damaged permanently.
Cloud-based data breach prevention is an effective way to safeguard data from unauthorized access, theft, or damage. Cloud-based solutions have several advantages over traditional methods, including scalability, affordability, and accessibility. The multi-layer security system offered by cloud-based solutions provides a robust defense against data breaches.
Common Types Of Data Breaches
Explanation Of The Various Types Of Data Breaches
Data breaches can happen in many forms, and it’s vital to understand each type to take adequate precautions. Here are some of the most common types of data breaches:
- Phishing attacks: This type of breach occurs when attackers trick users into sharing sensitive information like login credentials, by sending fake emails or messages.
- Malware attacks: Malware, or malicious software, is a type of computer program that cybercriminals use to intrude into and harm a computer system.
- Unintentional data exposure: This type of breach is caused by human error, such as accidentally sending sensitive information to the wrong recipient.
- Physical loss or theft: This type of breach happens when physical devices like laptops, usbs, or hard drives that contain sensitive information are either lost or stolen.
Examples Of Each Type Of Data Breach
To get a better understanding of the different types of data breaches, let’s look at some examples of each one:
- Phishing attack: An employee receives an email from what appears to be a legitimate source asking them to click on a link that will redirect them to a fake website with the intention of stealing their login credentials.
- Malware attack: A hacker sends an infected email attachment to a user, which when opened will install malware onto their computer allowing the attacker to access their data and sensitive information.
- Unintentional data exposure: An employee accidentally shares a spreadsheet containing sensitive customer data instead of sharing it only with authorized individuals.
- Physical loss or theft: A laptop containing sensitive data is stolen from an employee’s car.
Importance Of Understanding The Different Types Of Breaches To Better Prevent Them
Understanding the different types of data breaches is crucial for taking the necessary precautions to prevent them. By knowing what kinds of breaches can happen, one can take proactive steps to fortify data security. It is also essential to train employees on the importance of data security best practices, including identifying potential phishing scams and storing data in secure locations.
Regular security assessments for identifying areas of weakness and implementing data encryption and robust security protocols can ensure that your company’s valuable data stays safe and secure.
Best Practices For Cloud-Based Data Breach Prevention
Importance Of Compliance Regulations
Cloud computing has revolutionized data storage and made it more efficient and cost-effective. However, with the increase in data storage and sharing comes the risk of data breaches. Compliance with industry standards, such as hipaa and gdpr, is a critical aspect of preventing cloud-based data breaches.
To ensure that your cloud infrastructure is compliant, keep these points in mind:
- Review and follow industry-specific guidelines for data security.
- Implement strict access controls, like access management policies.
- Have regular audits of your system compliance with regulations.
Strategies For Implementing Strong Passwords And Multi-Factor Authentication
Passwords are the front line of defense against data breaches. Creating complex passwords that include letters, numbers, and symbols is crucial. Multi-factor authentication (mfa) adds another layer of security by requiring a user to present two or more pieces of evidence to verify their identity.
To implement strong password and mfa policies:
- Use a password manager to generate strong passwords that include letters, numbers, and symbols.
- Require mfa for all users accessing sensitive data.
- Use encryption and hashing to protect passwords as well as protect authentication details transmitted between servers.
Monitoring And Reporting Data Access And Usage
Monitoring and reporting data access and usage is a critical aspect of cloud-based data breach prevention. Regular monitoring of system activity can alert you to any suspicious activity.
To implement effective monitoring and reporting:
- Use monitoring and logging tools to detect anomalous user activity.
- Keep records of all logged-in users and restrict user permissions.
- Have designated administrators to monitor and report on activity.
Limiting User Access And Permissions
Limiting user access and permissions is another critical factor in data breach prevention. Restricting user access is a simple yet effective measure to protect data.
To implement effective user access and permissions:
- Implement the principle of least privilege.
- Use identity and access management tools (iams) to restrict access to data.
- Conduct regular reviews of privileges and remove those that are unnecessary.
Importance Of Employee Training And Awareness
Employees can unknowingly cause data breaches through their actions, so employee training and awareness are essential aspects of cloud-based data breach prevention.
To create an effective employee training and awareness program:
- Create strict guidelines for the use of mobile devices connected to the cloud.
- Educate employees on the importance of compliance with cloud security regulations.
- Regularly train employees in cybersecurity best practices.
Data breach prevention in the cloud is crucial in protecting sensitive information. By implementing the best practices mentioned above, any organization can ensure its cloud infrastructure is secure, compliant and robust.
Frequently Asked Questions Of Data Breach Prevention In The Cloud: Safeguarding Your Data
How Can I Prevent A Data Breach In The Cloud?
To prevent a data breach in the cloud, implement strong access controls, use encryption, monitor activity, and train employees on security best practices.
What Are The Risks Of Not Safeguarding My Data In The Cloud?
Not safeguarding data in the cloud can lead to data breaches, loss of sensitive information, damage to business reputation, and legal and financial repercussions.
Is It Safe To Store My Data In The Cloud?
Yes, it is safe to store data in the cloud as long as proper security measures are in place such as encryption, access controls, and monitoring of activity.
Conclusion
As cloud computing continues to become a powerful tool for businesses, ensuring data security in the cloud should be a top priority. With various security levels and measures in place, keeping data safe can be a daunting task for organizations.
However, by implementing some preventative measures, such as choosing a reputable cloud service provider and implementing solid security protocols, companies can safeguard sensitive information and prevent data breaches. Additionally, active monitoring and tracking user activities, as well as regular updates and patch management, can help in reducing the risk of data loss.
In the end, staying vigilant and proactive in guarding data in the cloud can help mitigate any potential threat, and ensure a secure storage environment for all business operations. With all this in mind, taking the necessary steps to secure data in the cloud should be a priority for all businesses.